Information Security Policy
In order to ensure the implementation, effective operation, supervision, and continuous management of the company’s information security management system, and to maintain the confidentiality, integrity, and availability of the company’s critical information systems, this information security policy is hereby issued. The purpose of this policy is to provide clear guiding principles for all employees in their daily work. All employees are obligated to actively participate in the promotion of the information security policy to ensure the security and operation of the company’s data, information systems, equipment, and networks. It is expected that all employees will understand, implement, and maintain the policy to achieve the goal of continuous information operations.
"Implement information security and strengthen service quality"
"Strengthen risk management to ensure continuous operation"
"Prepare for emergencies and ensure rapid disaster recovery"
"Reasonable use of personal data and prevention of data leakage"
Implement information security and strengthen service quality
Ensure that all employees implement the information security management system, where all information-related measures should guarantee the confidentiality, integrity, and availability of business data. This is to prevent risks such as leakage, damage, or loss due to external threats or internal mismanagement. Appropriate protective measures should be chosen to reduce risks to an acceptable level. Continuous monitoring, review, and auditing of the information security system should be carried out to enhance service quality and improve service standards.
Strengthen risk management to ensure continuous operation
Supervise all employees in implementing information security management tasks, continuously conduct appropriate information security training, and establish the concept of "Information Security, Everyone's Responsibility." This aims to make employees understand the importance of information security, encourage compliance with information security regulations, improve information security awareness and emergency response capabilities, reduce cybersecurity risks, and achieve the goal of continuous operation.
Prepare for emergencies and ensure rapid disaster recovery
Establish emergency response plans and disaster recovery plans for critical information assets and key business operations, and regularly conduct drills for various emergency response processes. This ensures that in the event of a system failure or a major disaster, rapid recovery can be achieved to ensure the continuous operation of critical business functions and minimize losses.
Reasonable use of personal data and prevention of data leakage
Classify and assess personal data to determine the protection requirements and measures. Establish access control mechanisms, utilize encryption and security measures for the transmission and sharing of personal data, regularly evaluate compliance capabilities of third parties, and sign contracts and agreements with outsourced vendors to ensure personal data security (pending review). Strengthen employee training to raise awareness of personal data protection. Establish monitoring and auditing mechanisms to continuously track the use, access, and transmission of personal data, and respond promptly to any abnormal activities or security incidents. Ensure that when personal data is no longer needed, it can be securely and permanently deleted.
Information Security Management System
Our company's Information Security Management System (ISMS) follows the continuous improvement P.D.C.A. cycle management model established by the International Organization for Standardization (ISO). This model integrates and strengthens the information security management framework, establishing an institutionalized, documented, and systematized management mechanism. We continuously monitor and review management performance to implement the principles of information security management and business continuity. The goals are as follows:
- Implement information and communication security management policies.
- Fully integrate the Information Security Management System (ISMS).
- Train personnel on information and communication security expertise.
- Strengthen the information security environment and incident response capabilities.
- Achieve the measurement indicators of the information security management policy.
Ensure the confidentiality, integrity, and availability of the company's information assets, in compliance with relevant laws and regulations, protecting them from intentional or accidental threats from both internal and external sources, thereby safeguarding the rights and interests of the company's staff and customers.
The company implemented the ISO 27001 Information Security Management System (ISMS) in 2014 and has regularly obtained certification. The current certificate is valid from April 19, 2023, to August 31, 2025. In accordance with the ISO 27001 ISMS standards, the company has established an information security management system, formulated an information security policy, and developed specifications for system implementation, operation, monitoring, review, and continuous improvement. The information security management policy and objectives are based on the company's business activities and associated risks.
Information Security Organizational Structure
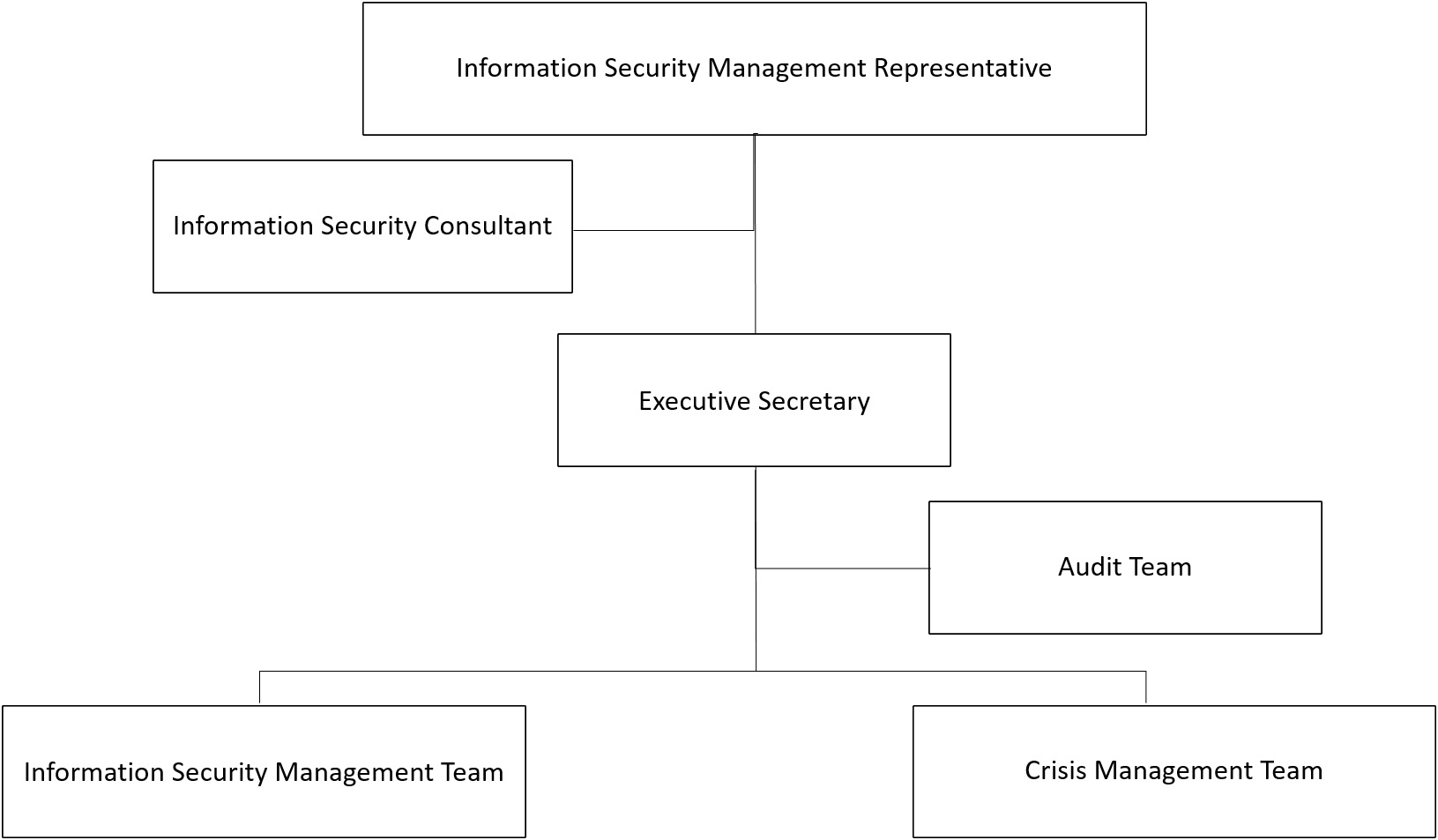
Information Security Management Team: The team consists of 4 members responsible for planning and executing various information security operations.
Crisis Management Team: The team consists of 9 members, organized into task groups, and is composed of relevant business personnel.
The Information Security Management Committee holds at least one meeting annually. In 2023, the committee convened to review the current information security management system of the company to ensure that the procedures are suitable, appropriate, and effective in meeting the company's needs. The committee also evaluates opportunities for improvement in related policies and objectives, or any other necessary changes. The review results should be documented and recorded for reference. This policy should be immediately reviewed if significant changes occur, ensuring its appropriateness and effectiveness. If necessary, relevant units and cooperating vendors should be informed to ensure joint compliance.